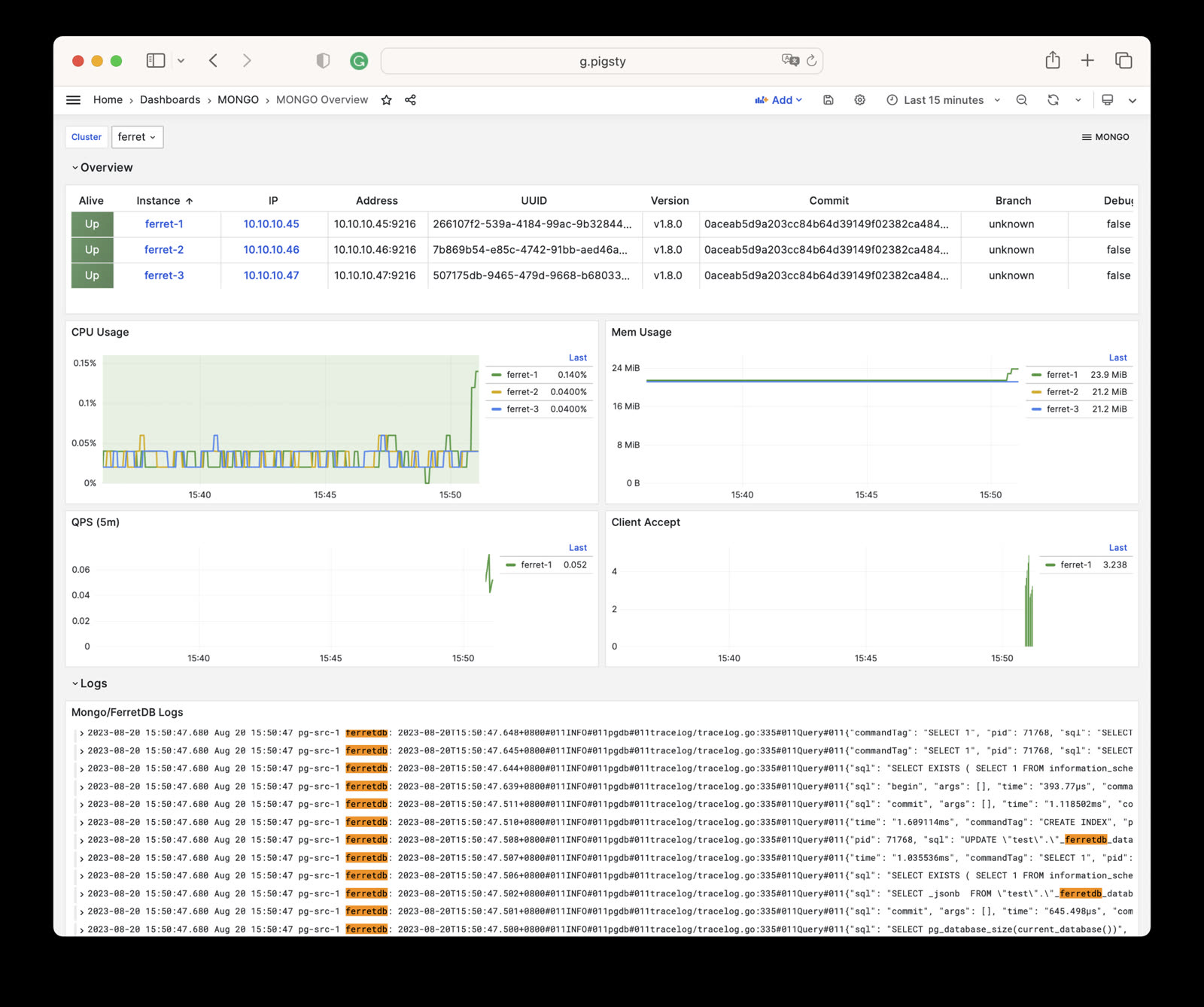
| ferretdb_client_accepts_total | Unknown | error, cls, ip, ins, instance, job | N/A |
| ferretdb_client_duration_seconds_bucket | Unknown | error, le, cls, ip, ins, instance, job | N/A |
| ferretdb_client_duration_seconds_count | Unknown | error, cls, ip, ins, instance, job | N/A |
| ferretdb_client_duration_seconds_sum | Unknown | error, cls, ip, ins, instance, job | N/A |
| ferretdb_client_requests_total | Unknown | cls, ip, ins, opcode, instance, command, job | N/A |
| ferretdb_client_responses_total | Unknown | result, argument, cls, ip, ins, opcode, instance, command, job | N/A |
| ferretdb_postgresql_metadata_databases | gauge | cls, ip, ins, instance, job | The current number of database in the registry. |
| ferretdb_postgresql_pool_size | gauge | cls, ip, ins, instance, job | The current number of pools. |
| ferretdb_up | gauge | cls, version, commit, ip, ins, dirty, telemetry, package, update_available, uuid, instance, job, branch, debug | FerretDB instance state. |
| go_gc_duration_seconds | summary | cls, ip, ins, instance, quantile, job | A summary of the pause duration of garbage collection cycles. |
| go_gc_duration_seconds_count | Unknown | cls, ip, ins, instance, job | N/A |
| go_gc_duration_seconds_sum | Unknown | cls, ip, ins, instance, job | N/A |
| go_goroutines | gauge | cls, ip, ins, instance, job | Number of goroutines that currently exist. |
| go_info | gauge | cls, version, ip, ins, instance, job | Information about the Go environment. |
| go_memstats_alloc_bytes | gauge | cls, ip, ins, instance, job | Number of bytes allocated and still in use. |
| go_memstats_alloc_bytes_total | counter | cls, ip, ins, instance, job | Total number of bytes allocated, even if freed. |
| go_memstats_buck_hash_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes used by the profiling bucket hash table. |
| go_memstats_frees_total | counter | cls, ip, ins, instance, job | Total number of frees. |
| go_memstats_gc_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes used for garbage collection system metadata. |
| go_memstats_heap_alloc_bytes | gauge | cls, ip, ins, instance, job | Number of heap bytes allocated and still in use. |
| go_memstats_heap_idle_bytes | gauge | cls, ip, ins, instance, job | Number of heap bytes waiting to be used. |
| go_memstats_heap_inuse_bytes | gauge | cls, ip, ins, instance, job | Number of heap bytes that are in use. |
| go_memstats_heap_objects | gauge | cls, ip, ins, instance, job | Number of allocated objects. |
| go_memstats_heap_released_bytes | gauge | cls, ip, ins, instance, job | Number of heap bytes released to OS. |
| go_memstats_heap_sys_bytes | gauge | cls, ip, ins, instance, job | Number of heap bytes obtained from system. |
| go_memstats_last_gc_time_seconds | gauge | cls, ip, ins, instance, job | Number of seconds since 1970 of last garbage collection. |
| go_memstats_lookups_total | counter | cls, ip, ins, instance, job | Total number of pointer lookups. |
| go_memstats_mallocs_total | counter | cls, ip, ins, instance, job | Total number of mallocs. |
| go_memstats_mcache_inuse_bytes | gauge | cls, ip, ins, instance, job | Number of bytes in use by mcache structures. |
| go_memstats_mcache_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes used for mcache structures obtained from system. |
| go_memstats_mspan_inuse_bytes | gauge | cls, ip, ins, instance, job | Number of bytes in use by mspan structures. |
| go_memstats_mspan_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes used for mspan structures obtained from system. |
| go_memstats_next_gc_bytes | gauge | cls, ip, ins, instance, job | Number of heap bytes when next garbage collection will take place. |
| go_memstats_other_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes used for other system allocations. |
| go_memstats_stack_inuse_bytes | gauge | cls, ip, ins, instance, job | Number of bytes in use by the stack allocator. |
| go_memstats_stack_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes obtained from system for stack allocator. |
| go_memstats_sys_bytes | gauge | cls, ip, ins, instance, job | Number of bytes obtained from system. |
| go_threads | gauge | cls, ip, ins, instance, job | Number of OS threads created. |
| mongo_up | Unknown | cls, ip, ins, instance, job | N/A |
| process_cpu_seconds_total | counter | cls, ip, ins, instance, job | Total user and system CPU time spent in seconds. |
| process_max_fds | gauge | cls, ip, ins, instance, job | Maximum number of open file descriptors. |
| process_open_fds | gauge | cls, ip, ins, instance, job | Number of open file descriptors. |
| process_resident_memory_bytes | gauge | cls, ip, ins, instance, job | Resident memory size in bytes. |
| process_start_time_seconds | gauge | cls, ip, ins, instance, job | Start time of the process since unix epoch in seconds. |
| process_virtual_memory_bytes | gauge | cls, ip, ins, instance, job | Virtual memory size in bytes. |
| process_virtual_memory_max_bytes | gauge | cls, ip, ins, instance, job | Maximum amount of virtual memory available in bytes. |
| promhttp_metric_handler_errors_total | counter | job, cls, ip, ins, instance, cause | Total number of internal errors encountered by the promhttp metric handler. |
| promhttp_metric_handler_requests_in_flight | gauge | cls, ip, ins, instance, job | Current number of scrapes being served. |
| promhttp_metric_handler_requests_total | counter | job, cls, ip, ins, instance, code | Total number of scrapes by HTTP status code. |
| scrape_duration_seconds | Unknown | cls, ip, ins, instance, job | N/A |
| scrape_samples_post_metric_relabeling | Unknown | cls, ip, ins, instance, job | N/A |
| scrape_samples_scraped | Unknown | cls, ip, ins, instance, job | N/A |
| scrape_series_added | Unknown | cls, ip, ins, instance, job | N/A |
| up | Unknown | cls, ip, ins, instance, job | N/A |